Consistent data protection starts with monitoring
…and not with general phrases in data protection texts in order to comply with laws
We also follow reports of cyber attacks and ransomware on authorities and companies every day. But what we don't understand: How can such incidents occur despite IT audits, external consultants and security concepts? Presumably because much of it was not implemented consistently and conscientiously due to time pressure or because it was not checked by an independent party.
Classic IT in micro and small companies usually has 3 problems, which can have a significant impact on ongoing operations and can subsequently become significantly more expensive than if handled proactively:
small budgets
IT rarely gets the appreciation because it is viewed purely as a cost center and not as a revenue generator like marketing or sales. It is often forgotten that good IT can achieve a very good return on investment.few staff
In IT "everything is the same" anyway - you realise this at the latest when you see the job advertisements and and the requirement profiles they contain. Have you ever met a translator who speaks Russian, Mandarin and Hindi? We haven't yet.high time pressure
IT receives attention when something doesn't work as it should or there is pressure from outside, e.g. cyber security incidents or reporting, then it is best to deliver the day before yesterday instead of proactive further development.At the latest when an incident occurs, companies are susceptible to inflated prices and sparklers without knowing what service is actually being provided by the external service provider in question. They also like to relabel Open source solutions or the actual work is outsourced to low-wage countries without informing the customer in the interests of transparency.
Our recommendation: Define the scope of services precisely, check the general terms and conditions and pay particular attention to the issue of liability. If an external service provider takes care of your IT security, they should also be held liable for the respective scope - provided the incident can be proven to be attributable to them.
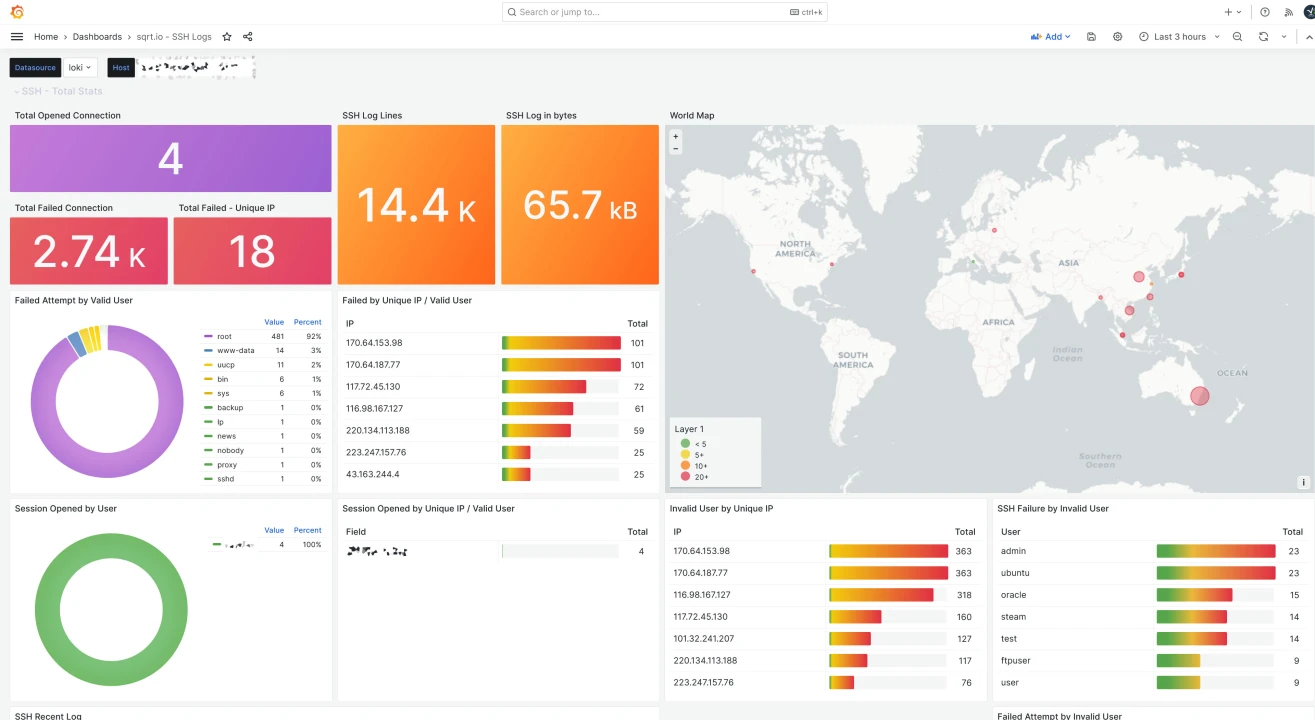
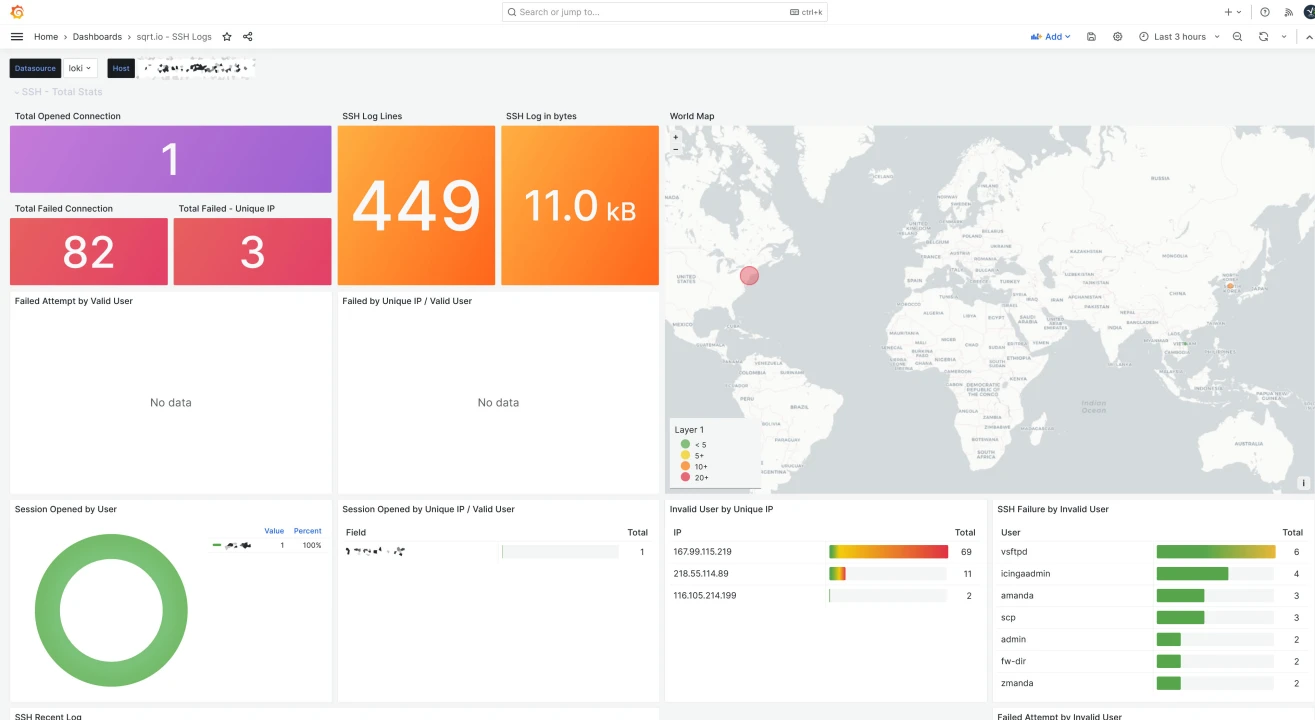
Independent - and ideally tamper-proof - monitoring makes sense, especially when it comes to the "liability issue". Monitoring also helps to demonstrate whether measures have been implemented and whether they actually made sense or not. As an example below you will find monitoring of SSH access without Crowdsec and with Crowdsec firewall bouncer.
Then just implement an interface.*
*Classic statement without IT background knowledge
As a consequence, in the chain of responsibility between the budget, actual implementation and review of the measures, if an incident occurs, the hot potato is passed on until there are no longer any consequences to fear. To the outside world, you are always a “victim of a cyber attack” because shifting responsibility to an intangible place is still the most elegant way from a PR and marketing perspective.
From our point of view, stereotypes and nationalities have no place in the media or when it comes to hacking. Hackers don't just come from Russia or China and generally wear dark hoodies. For better understanding and differentiation, we use different nationalities and real-world examples below.
If you have now become a victim of classic ransomware, you can at least check based on the address of the Bitcoin wallet whether a Russian group is “actually” behind the extortion. In the best case scenario, in the event of a classic break-in, there is the IP address - provided the log files have not been deleted.
However, an IP address is comparable to a vehicle license plate: just because your video surveillance captured a vehicle with Russian license plates does not mean that the occupants are also Russian. So if the thieves have a certain level of intelligence, they will try to disguise their true origins as best as possible.
This is applied to IT with VPN over several servers without logging, e.g. Wireguard/OpenVPN implemented. Alternatively, there are of course enough VPN providers where the respective country can be easily selected. In private environments it is also often used to circumvent censorship and geo-blocking or to maintain privacy.
As a result, affected companies should see themselves less as victims after an incident, but rather use the opportunity to critically question internal structures and processes - similar to the garden gate mentioned above: Did we fail to modernize (in time) or was there more talk than agile implementation?
The protection of your personal data is particularly important to us. We therefore process your data exclusively on the basis of the legal provisions (GDPR, TKG 2003).
Laws definitely have their place in the sense of fair “rules of the game” for everyone involved. Likewise, consulting services, structural analyses, concepts, standardization or coordination discussions - provided the framework conditions are right and concrete implementation measures are defined.
A bad example of the relationship between the individual sub-areas can be seen in the diagram according to the motto "The main thing is a lot of paper" paired with generic statements à la "state of the art" - the interpretation is therefore left to those involved.
However, technology does not interpret, technology does according to the specifications of parameters and algorithms.
A 9 therefore remains a 9 and does not become a 6 - depending on the perspective from which the person looks at the number. Blue is recognized as blue - within the specified limits and parameters - and does not turn purple.
AI is a little more tolerant of probability calculations based on models: if you photograph a tree, you will get a probability as a result: tree (74%), shrub (16%), flower (9%) and other (1%). It then depends on further processing whether the user is shown the probability or only the result with the highest probability.
Technology and IT therefore remain the most honest and incorruptible feedback providers of those mentioned above paperwork. A current example is the problem of the German Bundeswehr (Taurus wiretapping affair) name: Despite a lot of paper with regulations, simple basics were more or less "forgotten". More celebrities Examples are Mercedes with the Source Code Leak or the Storm-0558 Hack at Microsoft.
Meaningful Investments
Our three suggestions focus on the human factor with the aim of becoming more attractive as an employer again. Based on critical employer reviews (1 to 3 stars) from Kununu on the topics: 9 to 5, dusty software, fruit basket and “My manager has no idea what we’re actually doing.”
Trainings
Meaningful training does not start with high technology, but with "boring" basics, because only those who understand the basics can understand more complex topics on this basis.It is not for nothing that the first step involves the basic arithmetic operations of addition, subtraction, multiplication and division taught and equations follow based on this knowledge.
Agility
Less paper is not only good for the environment but also helps with implementation - works well in aviation with preflight checklists as long as you like statisticsHowever, in addition to a fixed annual budget, agility also requires a variable budget for unforeseen events and sensible further developments.
Automation
Automation makes sense wherever there are recurring, standardized processes, such as: Updates, data maintenance/data storage or even in the following scenario:The printer informs you about empty toner via email and you give the system permission to order from the "regular supplier" - or the cheapest provider.
SSH login monitoring
In our opinion, a basic for Linux servers includes a firewall with dynamic rules and SSH monitoring. The time required to implement Crowdsec with nftables is kept to a minimum thanks to Docker Compose and lots of free tutorials within limits.
In this case, vector.dev is used to prepare and further transfer the log files and sent to Loki handed over. The visualization is done by Grafana. Of course there are also other solutions such as: Fail2Ban (dynamic firewall rules based on log files) or ELK (Elasticsearch, Logstash and Kibana) for recording and evaluation - depending on personal preference and requirements.
In the jargon of a study: The difference in the comparison period of 3 hours (10:00 p.m. - 1:00 a.m.) is obvious and proves the usefulness of the measure. Interested readers can form their own opinion on the topic of “geo bashing”.
Of course, we are always happy to receive constructive criticism of the article.
New project or
dissatisfied with the current IT costs? Write
to us for a free 30 minute initial
consultation via telephone or Microsoft Teams.